Cybersecurity That Saves Lives: A Healthcare Security Success Story

Cybersecurity is the practice of defending systems, networks, and software from malicious digital attacks. These attacks often aim to access, modify, or destroy sensitive information, steal money through ransomware, or disrupt normal operations.
Implementing strong cybersecurity practices has become more complex today because there are now more devices connected to the internet than there are people, and attackers continue to evolve their techniques.
A strong cybersecurity strategy involves multiple layers of defense that cover the devices, networks, applications, and data you want to protect. Within an organization, a well-integrated security system can automate many aspects of detection, investigation, and response, helping security teams identify threats faster and take corrective action efficiently. An effective defense requires alignment between three elements: people, processes, and technology.
People
Users play a critical role in security. They must follow basic principles for data protection and privacy, such as creating strong passwords, being cautious with email attachments, and backing up data regularly. Good cybersecurity starts with well-informed individuals who know how to avoid common risks.
Processes
Organizations need a well-defined framework for responding to both attempted and successful cyberattacks. The NIST Cybersecurity Framework is a widely recognized model that helps businesses:
- Identify potential threats
- Protect systems and data
- Detect breaches and malicious activities
- Respond quickly to minimize damage
- Recover and restore normal operations
Having these processes in place ensures that cybersecurity is systematic and consistent.
Technology
Technology provides the tools needed to protect users and organizations from cyber threats. Security measures must cover three main areas:
- Endpoint Devices: Computers, mobile devices, and routers
- Networks: Protecting the flow of information between devices
- Cloud Environments: Safeguarding hosted applications and data
Common tools used for protection include next-generation firewalls, DNS filtering, malware detection, antivirus programs, and secure email solutions.
Why Cybersecurity Is Important
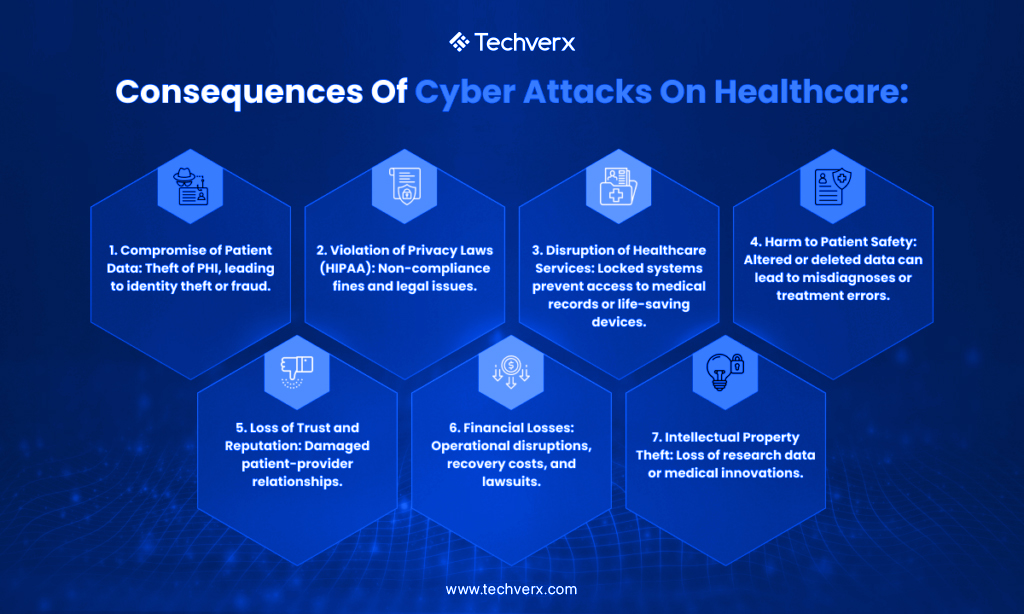
Cybersecurity impacts everyone in our connected world. At a personal level, cyberattacks can lead to identity theft, blackmail attempts, or loss of valuable data like family photos. At a societal level, we all depend on critical infrastructure—power plants, hospitals, banks, that must remain secure to keep communities running.
Cyberthreat research teams worldwide play an essential role by discovering new vulnerabilities, analyzing emerging threats, and educating the public. Their work helps make the internet a safer place for all.

Types of Cybersecurity Threats
Cloud Security
Cloud security focuses on fast detection and resolution of threats while maintaining visibility and control across multiple cloud platforms. It safeguards applications, data, and users without reducing productivity, an essential requirement for hybrid and remote work setups. Because cloud use continues to expand, cloud security must scale to protect a growing number of users, devices, and applications.
Identity Security
Identity and access management protects digital identities belonging to individuals, devices, and organizations. It ensures:
- Authentication: Verifying that users are who they claim to be
- Authorization: Allowing access only to the resources that users are entitled to
- Monitoring: Tracking activity to detect suspicious behavior or weak security postures
When implemented correctly, identity security makes it possible to balance protection with smooth, productive access.
Malware
Malware is malicious software designed to infiltrate systems, steal data, or cause damage. Strong malware protection can block these programs before they spread.
Phishing
Phishing attacks involve fraudulent emails that look like they’re from trusted senders. The goal is to trick recipients into sharing sensitive information such as login credentials or credit card numbers. Education and robust email filtering tools are key defenses against phishing attempts.
Ransomware
Ransomware is malicious software that locks users out of their systems or data until a ransom is paid. Even if payment is made, there is no guarantee that files will be restored making prevention and backup strategies essential.
Social Engineering
Social engineering manipulates people into giving away sensitive data, clicking harmful links, or taking actions that benefit attackers. This technique often complements phishing, malware, or other attacks to make them more convincing.
Threat Detection
An effective detection and response system collects information from across the security infrastructure, giving analysts a clearer picture of what’s happening. This helps prioritize incident response, surface previously unnoticed attacks, and stop threats before they spread further.
Zero Trust
Zero trust is a security strategy, not a single product. It is built on the principle of “never trust, always verify,” requiring continuous authentication and authorization of users and devices. A zero-trust approach typically involves:
- Multi-factor authentication (MFA)
- Device health checks
- Network segmentation
- Secure, controlled access to company resources
This approach minimizes the risk of unauthorized access, even from within the network.
Best Practices for Cybersecurity
Adopting best practices significantly reduces the risk of falling victim to cyberattacks. Three key recommendations include:
- Keep software and systems updated: Regular updates patch vulnerabilities and enhance protection.
- Use strong, unique passwords: Weak or reused passwords are a common entry point for attackers.
- Enable multi-factor authentication: Adding a second verification step greatly reduces the chance of unauthorized account access.
Staying informed about new threats and security measures is critical to staying one step ahead of cybercriminals.
Innovative Cybersecurity Solutions
Techverx offers a comprehensive cybersecurity division dedicated to helping businesses stay secure, resilient, and audit-ready. With our deep technical expertise and a tailored approach, we deliver proactive, end-to-end protection that goes beyond compliance, combining regulatory insight with security strategies designed around your unique operations.
Core Cybersecurity Solutions
Internal & External Penetration Testing
Techverx simulates real-world attacks on both internal and external systems to uncover vulnerabilities before malicious actors can exploit them. These tests strengthen defenses from every angle.
Vulnerability Scanning & Assessments
Our continuous scanning solutions detect and evaluate weaknesses across your environment, helping you stay ahead of potential threats.
Risk Assessments
We help you prioritize critical assets by assessing threats, impacts, existing controls, and risk exposure — ensuring you focus on protecting what matters most.
Continuous Support & Remediation Services (vCISO)
Gain access to ongoing cybersecurity guidance from Techverx experts. Our virtual CISO (vCISO) services provide strategic direction and rapid response to improve security posture and address emerging risks.
MDR & EDR
Our Managed Detection & Response (MDR) and Endpoint Detection & Response (EDR) services continuously monitor networks and endpoints, identifying, investigating, and neutralizing threats in real time.
Incident Response
Techverx’s Security Operations capabilities ensure fast detection, containment, and resolution of security incidents — minimizing downtime and protecting business continuity.
Audit Partner Ecosystem
We connect you with trusted audit partners, offering personalized support to streamline compliance efforts and provide holistic oversight for risk management.
Cybersecurity Insurance
Through our network of insurance partners, we help you strengthen your security posture and prepare for potential incidents, reducing recovery time and financial exposure.
Compliance Readiness Examinations
Techverx evaluates your security framework against regulatory standards to ensure you are fully prepared for audits and can demonstrate compliance with confidence.
Social Engineering Testing
Our team simulates real-world phishing, impersonation, and social engineering tactics to assess employee awareness, uncover human vulnerabilities, and strengthen your first line of defense.
Disaster Recovery Testing
We regularly test your disaster recovery plans by simulating real disruptions, validating your ability to restore critical systems and data quickly to minimize operational downtime.
Security Configuration Reviews
Techverx reviews and optimizes system configurations to enhance security controls and reduce exploitable weaknesses across your infrastructure.
Case Study: United Organ Services
United Organ Services has long been a key player in organ and tissue donation, supporting lifesaving work across the healthcare ecosystem. As technology and cybersecurity threats evolved, the organization recognized the need to modernize its IT infrastructure and strengthen its security posture. This case study highlights United Organ Services’s collaboration with Techverx and the transformation that followed.
Background & Engagement with Techverx
When United Organ Services first engaged with Techverx, their IT environment was difficult to manage and lacked formal security processes. According to Jeshua Lack, Director of IT, they were “flying by the seat of our pants,” struggling with compliance requirements and operational efficiency.
Techverx guided the organization through a structured IT transformation, beginning with virtualization and DNS security to stabilize their infrastructure. Their proactive approach and responsive account management ensured smooth implementation and minimized disruption.
Strengthening Security & Compliance
A key milestone was the rollout of Security Posture as a Service, delivered by Techverx’s cybersecurity division. This solution created a clear, structured framework that:
- Plugged Security Gaps: Regular internal and external scans identified and resolved vulnerabilities.
- Simplified Compliance: Streamlined efforts to meet NIST, HIPAA, and UNOS standards.
- Enhanced Visibility: Security scores and compliance insights were shared in easy-to-read executive summaries, keeping leadership informed without overwhelming them.
The solution also eliminated the need to hire a dedicated CISO, freeing up budget to be invested in strategic security initiatives and collaborative improvements.
Outcomes
- Stronger Security Posture: Reduced vulnerabilities and improved risk management.
- Improved Communication: Executive-level summaries provided clarity and alignment.
- Operational Efficiency: Freed internal teams to focus on critical mission-driven initiatives.
- Cost Optimization: Avoided high CISO costs while maintaining expert oversight through ongoing vCISO support.
Conclusion
Through its partnership with Techverx, this leading organ and tissue donation network transformed its IT and security strategy, closing critical gaps, streamlining compliance, and freeing internal teams to focus on their mission. Techverx’s Security Posture as a Service and ongoing vCISO support provided a cost-effective, scalable approach to cybersecurity, enabling the organization to stay resilient, audit-ready, and focused on saving lives.
In a healthcare landscape where security and compliance are non-negotiable, Techverx continues to be a trusted partner, helping mission-driven organizations protect sensitive data and deliver on what matters most.
Ready to build your team of tomorrow? Talk to a Techverx consultant today
Hiring engineers?
Reduce hiring costs by up to 70% and shorten your recruitment cycle from 40–50 days with Techverx’s team augmentation services.
Related blogs